Simple Steps To Implement An Effective Base Layer in Your Small Business Security
A common misconception with small business IT security is that security costs $$$. Truth be told, most security issues lie in areas that are well within your control as a business owner or decision maker. Let us show you a few ways that you can make a significant impact to your small business cybersecurity posture without costing a lot of money.

Start With Simple Yet Effective Changes
Let’s start with some core security principles for small business IT security.
– Review your business on-boarding, off-boarding, and core policies and align them with simple IT security basics.
This may sound like a lot of work, but the effort you put into this step pays security dividends down the road for you.
Begin with reviewing your business policies and applying simple changes.
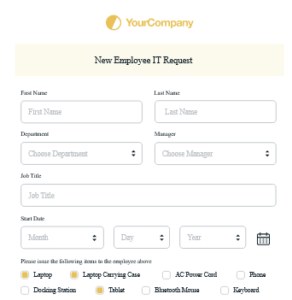
On-boarding and Off-boarding of employees
Ensure that you have a checklist of the steps required to bring on an employee, or in the event that things don’t work out, how to quickly and securely off-board an employee without missing important details.
This includes:
- A form that has fields that encapsulate the employee’s position, required permissions, mapped drives, printers and application access.
- A mirrored form for the off-boarding of an employee that is based on the on-boarding document.
- Document security elevations and changes. If you gave the employee additional access post-on boarding, you should document these changes to reference in the off-boarding document. Ideally, you have your permissions and mapped drives etc. contained within security groups so that you can remove the user from the group, thus removing the permissions.
- Outline the allowed use of technology in your business. This can be things like allowing non-company devices onto your network. Or accessing certain types of websites from company owned assets. And enforce these policies.
Define in your policies that your systems are monitored for inappropriate use. - Outline expectations on email usage. Encourage employees to watch for things like warnings that an email is external, and what to look for in those emails.
- How to report a security concern or issue. Let your staff know the best way to communicate a problem they might find, or if they have questions.
The Basics - Awareness, Zero Trust and Multifactor
Cover the Essentials
Make sure that, as a business owner, you communicate the importance of small business security to your management team and employees in your everyday interactions. Often, we observe management instructing employees that they “have” to complete a task to keep the owners or the Systems Administrator happy. This sets the wrong tone. Management should be actively involved in the security of the business, leaving no room for indifference.
Technical Minimums
Here are some of the most important tasks that need attention in all systems, with a particular focus on login authentication systems.
Limit Administrator Roles: Local administrator permissions are a ticking time bomb. Ensure that only those who absolutely require it have it, and make sure they understand that these accounts are only to be used for specific tasks.
System Administrators: They should use non-administrator accounts for day-to-day tasks and elevate privileges using a dedicated administrator account when necessary.
Managers, Directors, and Owners: They don’t need administrative access. If you have a dedicated manager on the floor who can authorize an installation, create a separate administrator account for that user and instruct them on how and when to use it. If you, as an owner, need to elevate your access, you should do it from another account that you use on occasion. Your main account doesn’t need this level of access.
Multi-factor Everything!: If possible, enable multi-factor authentication on line-of-business applications. This includes mail systems like Office 365, CRM systems, and external systems such as payroll apps or time trackers. If possible, outline an MFA method that can be shared across all systems, such as an Authenticator app or SMS if no other option exists.
Log and Enable Warnings/Errors: Log and enable warnings/errors in your infrastructure and applications. Even if you don’t have time to monitor logs and warnings daily, you can log and archive this information for reference in case of an event. We recommend partnering with an IT provider, such as Securiv, to do the monitoring for you and advise you when you need to make changes or take action based on the information you are collecting/warning on.
Understand Your Attack Surface!: An initial security consultation with an experienced IT security professional can help you identify how and where you are most vulnerable. Perhaps you use a client VPN solution that has a vulnerability, or your line-of-business application doesn’t support complex passwords/multi-factor authentication. Or you have a web application served to the internet that doesn’t have the required security monitoring in place. Understanding your weaknesses is an important initial step to a good security posture.
The Dilemma of Speed and Accuracy: Balancing Manufacturing Workflows with Small Business IT Security
In the fast-paced realm of manufacturing, where efficiency is paramount, companies often design workflows meticulously to prioritize speed and accuracy. While this approach fosters productivity and competitiveness, it may inadvertently pose challenges for small business IT security. This article explores the potential pitfalls and offers insights into achieving a delicate balance between streamlined manufacturing processes and robust cybersecurity measures.
1. Rapid Adoption of Technologies: Manufacturing companies eager to enhance efficiency often deploy cutting-edge technologies such as automation, IoT devices, and real-time monitoring systems. These technologies facilitate rapid production cycles but may introduce vulnerabilities if not properly secured. Ensuring that these tools adhere to robust cybersecurity standards becomes crucial to prevent unauthorized access and potential data breaches.
2. Limited Focus on Security Protocols: In a race to meet production targets, IT security might take a back seat. Manufacturing workflows designed for speed and accuracy may inadvertently sideline the implementation of comprehensive security protocols. This oversight can expose critical systems and sensitive data to cyber threats. Companies must recognize the importance of integrating security measures seamlessly into their operational processes.
3. Overreliance on Default Configurations: To expedite deployment, manufacturing systems are sometimes set up using default configurations. While this accelerates the onboarding process, it also leaves systems vulnerable to cyberattacks. Cybercriminals often target systems with default settings as they are well-known and easily exploitable. Customizing configurations and regularly updating security settings is crucial to thwart potential threats.
4. Insufficient Employee Training: In a high-speed manufacturing environment, employees may prioritize meeting production quotas over cybersecurity awareness. This can lead to unintentional security lapses, such as clicking on malicious links or neglecting proper password hygiene. Regular and tailored cybersecurity training programs are essential to educate employees on the importance of adhering to security best practices without compromising operational speed.
5. Supply Chain Vulnerabilities: Manufacturing companies with streamlined workflows often rely on a complex network of suppliers and partners. This interconnected supply chain introduces additional entry points for cyber threats. It is imperative for companies to vet and enforce cybersecurity standards across the entire supply chain, ensuring that vulnerabilities are not inadvertently introduced through third-party connections.
6. Data Privacy Concerns: Speedy manufacturing workflows generate vast amounts of sensitive data, ranging from proprietary designs to customer information. Protecting this data from unauthorized access or breaches becomes a significant challenge. Implementing encryption, access controls, and robust data governance policies is essential to safeguard sensitive information while maintaining operational efficiency.
Conclusion: In the pursuit of operational excellence, manufacturing companies must recognize the intrinsic link between speed, accuracy, and small business IT security. Striking a balance requires a proactive approach that integrates cybersecurity measures seamlessly into the fabric of manufacturing workflows. By acknowledging potential vulnerabilities and implementing robust security practices, companies can safeguard their operations, protect sensitive data, and maintain a competitive edge in an increasingly digitized manufacturing landscape.
Logs? What Logs? - The Crucial Role of Logging in Small Business Security and Infrastructure
In the ever-evolving landscape of cybersecurity, small businesses must be proactive in fortifying their defenses against potential threats. One often underestimated yet critical component in achieving robust security is the comprehensive logging of information. This article delves into the importance of logging in small business security and infrastructure, outlining how meticulous record-keeping can be a game-changer in safeguarding against cyber threats.
For small businesses aiming to fortify their security posture, implementing robust logging practices is not just a good practice; it is a necessity. Logging provides a wealth of information that can be instrumental in threat detection, incident response, compliance adherence, and overall infrastructure optimization. By recognizing the importance of meticulous log management, small businesses can create a resilient foundation for cybersecurity, safeguarding their operations and fostering trust with customers and stakeholders.
1. Early Detection of Anomalies: Logging plays a pivotal role in the early detection of suspicious activities or potential security breaches. By capturing and analyzing log data, small businesses can identify deviations from normal patterns, enabling swift responses to emerging threats. This proactive approach can significantly mitigate the impact of security incidents and reduce the risk of data breaches.
2. Forensic Analysis and Incident Response: In the unfortunate event of a security incident, detailed logs serve as a valuable resource for forensic analysis and incident response. Log records provide a chronological trail of events, helping cybersecurity professionals reconstruct the sequence of actions leading to a security breach. This information is instrumental in understanding the nature of the attack, identifying vulnerabilities, and implementing effective countermeasures to prevent future occurrences.
3. Compliance Requirements: Many industries and regulatory bodies mandate specific cybersecurity standards and compliance requirements for businesses, especially concerning the protection of sensitive data. Detailed logging practices help small businesses meet these regulatory obligations by providing evidence of adherence to security protocols. This not only ensures legal compliance but also enhances the overall trustworthiness of the business.
4. Proactive Monitoring and Prevention: Regularly monitoring logs allows small businesses to identify potential security weaknesses before they can be exploited. By analyzing log data, businesses can spot trends, pinpoint vulnerabilities, and implement preventive measures. This proactive approach is essential for staying one step ahead of cyber threats and maintaining a resilient security posture.
5. User Accountability and Behavioral Analysis: Logging user activities is crucial for establishing accountability within the organization. Detailed logs help track user actions, making it possible to attribute specific activities to individual accounts. This not only deters malicious insiders but also facilitates behavioral analysis, enabling businesses to identify and address any unusual or unauthorized activities promptly.
6. Infrastructure Performance Optimization: Logging extends beyond security concerns; it also plays a vital role in optimizing overall infrastructure performance. Monitoring system logs allows small businesses to identify bottlenecks, track resource usage, and troubleshoot performance issues. This proactive maintenance ensures that the business operates efficiently and minimizes the risk of disruptions.
Understanding Your Attack Surface: A Cornerstone of Small Business IT Security
In the dynamic landscape of small business IT security, understanding and mitigating the attack surface is a cornerstone for safeguarding digital assets and sensitive information. The attack surface represents all the points where an unauthorized user or a malicious actor could exploit vulnerabilities to compromise the security of a system. For small businesses, recognizing and comprehensively assessing this attack surface is crucial for developing a proactive and effective defense strategy.
The first step in understanding the attack surface involves identifying the various entry points that could be exploited by potential attackers. This includes not only traditional network endpoints but also web applications, cloud services, and interconnected devices. Conducting a thorough inventory of all assets and systems, both internal and external, provides a holistic view of the attack surface, enabling small businesses to pinpoint potential vulnerabilities.
Furthermore, a critical aspect of attack surface management is recognizing the diversity of potential threats. Small businesses often face a range of cyber threats, from external hackers attempting to exploit software vulnerabilities to insider threats posed by employees. By understanding the different vectors through which an attack can occur, businesses can tailor their security measures to address specific risks. This may involve implementing network firewalls, intrusion detection systems, and regular security training for employees.
Regular security consultations with experienced IT professionals can provide invaluable insights into a small business’s unique attack surface. These consultations involve in-depth assessments of systems, network configurations, and potential weak points. By collaborating with experts, small businesses can identify specific vulnerabilities that may go unnoticed and receive recommendations for mitigation strategies tailored to their operational environment and industry requirements.
Moreover, the attack surface is not static; it evolves with changes in technology, business processes, and external threats. Regularly revisiting and reassessing the attack surface is crucial for maintaining a proactive security posture. This involves staying informed about emerging cyber threats, updating security protocols, and adapting defenses to address evolving vulnerabilities. Small businesses should consider investing in threat intelligence services that provide real-time information about the latest cyber threats and vulnerabilities relevant to their industry.
In conclusion, understanding your attack surface is a foundational element of small business IT security. By identifying and assessing potential entry points, recognizing the diversity of threats, seeking professional insights, and maintaining a proactive approach to evolving risks, small businesses can fortify their defenses against cyber threats. In an era where digital assets are integral to business operations, a comprehensive understanding of the attack surface is not just a security measure but a strategic imperative for the sustained success of small enterprises in the digital landscape.
Summary - Simple, Yet Effective Steps to Secure Small Business
The focus of this blog post has been on fortifying small business security through various strategic measures. The importance of meticulous logging practices was highlighted as a crucial component, serving as a proactive defense mechanism against cyber threats. By enabling early detection of anomalies, facilitating forensic analysis, and ensuring compliance with industry regulations, comprehensive logging emerged as an invaluable tool for small businesses striving to maintain a resilient security posture. The articles emphasized that logging not only enhances cybersecurity but also contributes to infrastructure optimization, allowing businesses to operate efficiently while minimizing disruptions.
Another critical aspect addressed was the significance of a robust onboarding and offboarding process for small business security. These processes were underscored as essential safeguards against potential insider threats, data breaches, and operational disruptions. By implementing thorough onboarding procedures that include cybersecurity training, access control measures, and adherence to compliance standards, businesses can instill a security-conscious culture from the start. Additionally, a well-structured offboarding process ensures the swift revocation of access for departing employees, mitigating the risk of unauthorized data access and preserving operational continuity. These measures collectively contribute to the overall security resilience of small businesses.
In the context of small businesses, where resources are often limited, the articles also highlighted the delicate balance required between workflows designed for speed and accuracy and the imperative for robust small business IT security. Striking this balance entails addressing potential vulnerabilities in rapidly adopted technologies, maintaining a focus on security protocols, and ensuring employee awareness and training. Ultimately, the articles emphasized that a comprehensive approach to security, encompassing logging practices, on-boarding/off-boarding procedures, and a mindful integration of technology and workflows, is essential for the sustained success and resilience of small businesses in today’s digital landscape.